In the last 10 months I have added several minor features to the certificate verification management pack for SCOM 2012. Some of them rose from needs of clients but most were suggested by people using the MP. Many thanks for everyone providing feedback and especially for testing the pre-release builds.
You can head over to the SystemCenterCentral.com management pack calalog and download the updated MP version 1.3.0.0.
Changes in this update
The quick bullet list of improvements as also listed in the MP guide looks like this:
- Added Tasks: Archive Certificate, List Certificate Properties, Disable/Enable Monitoring, Rediscover
- Added Recoveries: Archive Certificate, Disable Monitoring
- Added Discovery: Web Hosting certificate store (Server 2012 / 2012 R2)
- Additional certificate property: Certificate Template. It is also listed on reports.
- Discovery filter expanded to certificate template.
- Alert description: Additional details on the certificate chain and SCOM action account used.
- CRL Lifetime Monitor: Threshold is exposed as an overridable parameter.
- CRL health roll up monitor added.
- Expiring certificate view & report: Default threshold of 1 month may be overridden.
- Views: Changed criteria on views to make them more reliable when using user scopes.
- Reporting bug: Certificate inventory did not list all certificates.
- Additional MP: Rediscovery Tasks. Immediate trigger of store content discovery after archive, disable/enable or rediscover tasks
And a few extra words on some of them
While some changes are pretty much self explanatory, I am going to give you some background information on others below. Plus two little PowerShell bits to make everyone’s lives a bit easier.
Added tasks
To make checking on the validity of certificates easier for SCOM operators, I have added agent tasks that will
- list certificate properties (and check validity)
- archive a certificate
- disable respectively re-enable monitoring for a single certificate (append friendly name tag)
- attempt immediate rediscovery
Archiving a certificate may obviously have a disastrous impact on payloads working with a certificate. However; it may be undone locally on an agent computer using some PowerShell code as in the following example:
#sample script to remove the ARCHIVED flag from certificates
#open personal computer store (read/write & include archived)
$store = New-Object System.Security.Cryptography.X509Certificates.X509Store "My","LocalMachine"
$storeOpenFlags = [System.Security.Cryptography.X509Certificates.OpenFlags]"ReadWrite, IncludeArchived"
$unarchive = New-Object System.Management.Automation.Host.ChoiceDescription "&Yes", "Set Archive Flag to 'false'"
$skip = New-Object System.Management.Automation.Host.ChoiceDescription "&No", "Keep archive flag"
$confOpt = [System.Management.Automation.Host.ChoiceDescription[]]($unarchive, $skip)
$store.Open($storeOpenFlags)
if ($store.StoreHandle) {
Write-Output ("Listing ARCHIVED certificates in store " + $store.Name)
$store.Certificates | where {$_.Archived -eq $true} | % {
$cert = $_
$cert | ft Thumbprint, Subject, Issuer
switch ($host.ui.PromptForChoice("Unarchive", "Remove 'ARCHIVED' flag from certificate?", $confOpt, 1))
{
0 { $cert.set_Archived($false)
if ($cert.Archived -eq $false) {Write-Output ("SUCCESS: Removal of ARCHIVED flag on certificate with thumbprint " + $cert.Thumbprint + " succeeded")}
else { Write-Output ("ERROR: Removing ARCHIVED flag on certificate with thumbprint " + $cert.Thumbprint + " failed"); continue }
}
}
}
}
else { Write-Output ("Failed to open store " + $store.Name) }
#don't forget to close store after operation
$store.Close()
Since there’s no undo option for deleted certificates, the MP does not contain a task to delete certificates.
Disabling monitoring for a single certificate is achieved by appending the tag “_DoNotMonitor” to the end of a certificate’s friendly name. Such certificates are then becoming members of a group and monitoring will stop by means of predefined overrides. Instead of using the SCOM task, a system administrator might simply use the certmgr snap-in to alter the friendly name.
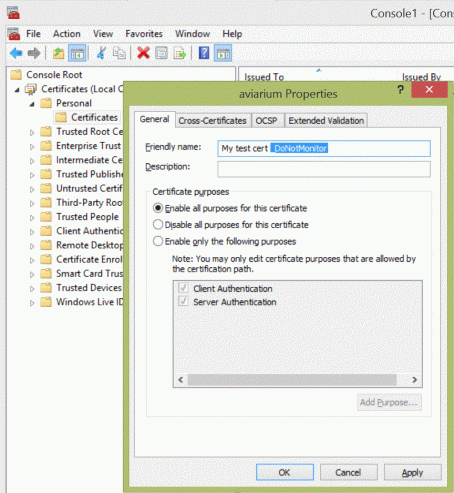
Tag friendly name to disable monitoring
The rediscovery task will only be available, if the additional MP ReDiscoveryTasks has been imported. It will run a management server side PowerShell script, triggering the SCOM task “Trigger On Demand Discovery Task“. Overrides will be accounted for. Such, changes to an agent’s certificate store will be reflected much more quickly in SCOM. The progress can easily be verified by checking the “Task Status” view. Note that the ReDiscoveryTasks MP will also attempt to run an OnDemand discovery after Archive and Enable/Disable tasks have been performed.
Added Recoveries
Two disabled recoveries have been added to the certificate monitors:
- Archive Certificate
- Disable Monitoring
They do behave exactly the same as the related tasks mentioned above. They will show their effect on the SCOM repository within minutes if the optional ReDiscoveryTasks MP is imported. Otherwise monitoring will not stop until the next discovery cycle has passed.
Added discovery of the Web Hosting store
Windows Server 2012 and 2012 R2 feature a new certificate store called “Web Hosting”. Behind the scenes it provides more load efficient certificate handling and is thought to be used e.g. with IIS in web hosting scenarios (what a surprise). When using the QuickStart override MP, those stores and all signed certificates in them will automatically be discovered.
Monitoring wise it is important to understand that this store is thought to hold hundreds of certificates. Hence thinking about a good filtering strategy for monitoring may crucial. Failing to do so could lead to way too many objects being discovered, causing performance issues on SCOM. Consider making use of the Subject, Issuer and Template filtering capabilities.
Certificate Template information
Certificates issued by Enterprise CAs can now be filtered based on their template name (and OID). Consequently, the template property has been added as an additional property to the certificate and will be listed on inventory reports.
It is important to understand that the names of certificate templates are specific to an AD forest. They cannot be resolved if such a certificates is located on a computer outside of the forest. In that case, the MP will display the template OID value only. To check what the template property of a certificate is, run the following PowerShell commands on an agent computer:
#gets template names (and/or OIDs) of local certificates
get-childitem cert:\LocalMachine\My | ft -Wrap Thumbprint, Subject, Issuer, @{Label="Template"; Expression={
$templateName = ""
#TemplateName (Version 1)
$_.Extensions | where { $_.OID.Value -match "^1\.3\.6\.1\.4\.1\.311\.20\.2$"} | % {
$templateName = $_.Format($false).trim()}
#Template (Version 2)
$_.Extensions | where { $_.OID.Value -match "^1\.3\.6\.1\.4\.1\.311\.21\.7$"} | % {
#sometimes no actual name but only the OID is contained
($_.Format($false)) -match 'Template=((?.+)\((?1\.3\.6\.1\.4\.1\.311\.[0-9.]+)\)|(?1\.3\.6\.1\.4\.1\.311\.[0-9.]+))' | Out-Null
if ($matches.templateName) {$templateName = ($matches.templateName.trim() + "(" + $matches.templateOID.trim() + ")")}
else {$templateName = $matches.templateOID.trim()}}
$templateName
}}
Updated Alert Description
The alert description of monitors has been overhauled to be much more verbose. Specifically it is now showing both the subject and the issuer property. It also contains information about the RunAs account used for monitoring and gives details on the validity of the certificate chain.
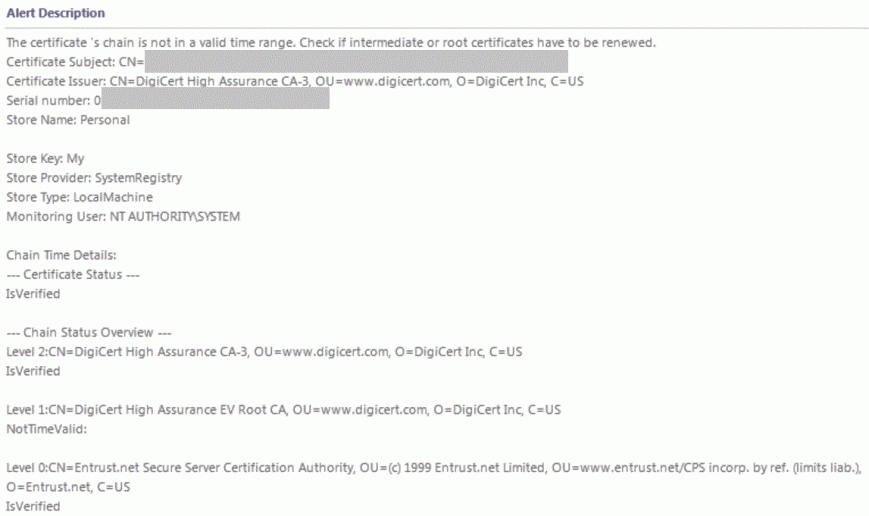
Alert description example: intermediate CA certificate has expired (Level 1)
Such it has become much easier to pinpoint issues when not the end certificate itself but a chain certificate has become invalid; possibly just in the context of the RunAs account of the agent.
An extra hint regarding the latter in case the agent is running under the local system account: Occasionally it can be observed that a certificate chain is reported invalid by the MP but is valid if a certificate is checked with an interactive user account. One possible reason for this can be the SYSTEM account not being able to automatically update CTLs (e.g. due to internet access restriction), while an interactive account can. If the issue cannot be resolved, consider using a tool like SysInternals PSExec.exe to launch the CertMgr.msc in the SYSTEM context to investigate the cause.
Download MP version 1.3.0.0 from SystemCenterCentral.com